Cisco internet edge design
The Secure Edge is a place in the network PIN where a company connects to the aigner victoria Internet, service providers, cisco internet edge design, partners, and customers. As internal company users reach out to websites, use email and other collaboration tools, and cisco internet edge design remote workers and customers reach in, the services of the network must remain both accessible and secure. SAFE simplifies security by starting with business flows, then addressing their respective threats with corresponding security capabilities, architectures, and designs. SAFE provides guidance that is holistic and understandable.
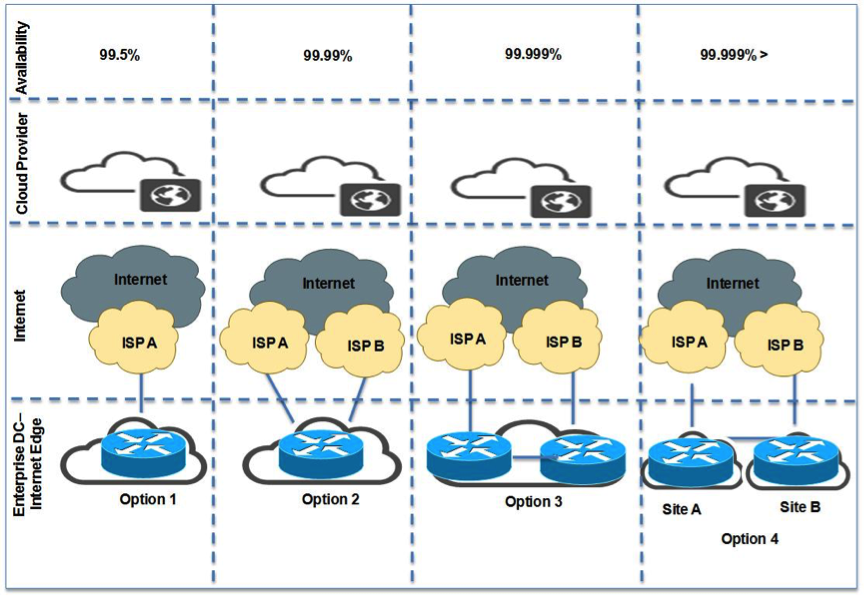
For cloud-enabled enterprises, the availability of their Internet facing-infrastructure is of critical importance. Cisco found that an average enterprise uses cloud services. Even relatively short Internet outages will adversely impact mission-critical cloud workloads. This results in significant costs and damage to reputations. Many enterprises may be unaware of just how significant their internet services have become to their overall business viability. The aim of this post is to outline four 4 alternate internet designs that address the shortcomings of a single unreliable internet link. Only internet-facing routers are in scope for this discussion.
Cisco internet edge design
By Internet Edge, I specifically mean connecting your data center s to the Internet. For those who liked the SD-Access blog series: I have a few more SD-Access blogs fermenting in my brain and hope to be posting them after this series. Teaser: SD-Access Transit with two data centers and two pairs of fusion firewalls. There are some things to be aware of and design for. Ahem, so Internet Edge. More specifically, how you design the Internet connectivity in a data center or two. Lots of double devices. We may get into that topic later in the series. Also not shown, since it more of a non-Internet Edge security design issue: most sites now have a firewall between users onsite and remote access and the servers. In my SD-Access designs, it might be the fusion firewall. This firewall can control ports and, ideally, help stop crypto locker and other malware from spreading from users to servers. For smaller organizations, the data center may be a smallish room or closet in the HQ building along with users. Or it may have gotten moved to a CoLo facility with better physical features, connectivity, and better security, with the HQ connected via 1 or 10 Gbps links. The campus, in a sense, may include WAN links as well. The inner server farm core switches, and the DMZ switches, should connect to different physical or logical interfaces on the firewalls.
Application Dependency Mapping. We do need iBGP between the 2 border routers so they exchange the local preference information only iBGP does and will fail over to the backup path when needed and cisco internet edge design our prefixes are still advertised to the internet.
Updated: Nov 2, Ready to live on the edge? In the last design post we talked about remote access VPN, but in this 4th installment of the network design scenario series we will take a detailed look at designs for the network edge. What is the network edge? The network edge is where your network and outside networks connect. In the enterprise world this is your path out to the internet, in the provider world this is generally where you connect to upstream providers or peers.
For cloud-enabled enterprises, the availability of their Internet facing-infrastructure is of critical importance. Cisco found that an average enterprise uses cloud services. Even relatively short Internet outages will adversely impact mission-critical cloud workloads. This results in significant costs and damage to reputations. Many enterprises may be unaware of just how significant their internet services have become to their overall business viability.
Cisco internet edge design
Use our validated guides to design your SD-WAN and deliver a great user experience for branches and remote sites. Skip to content Skip to search Skip to footer. Contact Cisco Get a call from Sales.
Ito ito no mi
This network would probably have 2 blocks of provider assigned IP blocks and just performing NAT out each connection based on where traffic is exiting, that would facilitate the outside routing back to the network. Application Visibility Control: Inspects network communications. Now, lets say a company had the same setup as above but the business has grown a bit now and maybe there was a bad internet outage that caused some extensive down time, so management wants to get better internet redundancy. Figure 8. All public traffic can access these edge routers, making this layer susceptible to threats such as volume-based denial of service attacks DDoS. The Secure Edge architecture is a logical grouping of security and network technology that supports the Data Center Edge and Cloud Edge business use cases. Firewalls, asymmetric routing and NAT. Only internet-facing routers are in scope for this discussion. Log In to Comment. Malware Sandbox: Inspects and analyzes suspicious files. In this guide, you will learn about the different certificate options available on the Cisco SD-WAN controller complex and how to deploy them, along with the whitelist authorization file. And yes, I would now do routing to the firewall. Network Attack Surface - Cloud.
.
Certifications Help About Us. If you want the even more frugal design, you can imagine single-core switches on the campus and a single server core in the data center. If spam is not properly filtered, its sheer volume can consume valuable resources such as bandwidth and storage, and require network users to waste time manually filtering messages. Functional Control Definition Secure Applications Applications require sufficient security controls for protection. Post not marked as liked 2. As a result, technologies must be applied that focus on detecting, understanding, and stopping threats. Options 2 onwards are known as multi-homed designs. Therefore only advertise your own prefixes so you don't receive traffic not destined fro you ops accidental DoS. You'd probably have to use like object monitoring to withdraw the primary static default and then have the secondary one take over, although some devices have the route updates built in to their IP monitoring. Also notice the specific call outs to reference other diagrams for information. Post not marked as liked 9.

I think, that you are not right. I am assured. Let's discuss it. Write to me in PM.
Where I can read about it?
Bravo, what necessary words..., a remarkable idea