Explotdb
BackTrack is a Linux-based penetration testing arsenal that aids security professionals in the ability explotdb perform assessments in a purely native environment dedicated to hacking, explotdb. The manuals section explotdb you with simple information in order to get up and running with Back Track and help with some additional features unique to the suite. Nmap —free open source tool for network analysis and security audits.
We will keep fighting for all libraries - stand with us! Search the history of over billion web pages on the Internet. Capture a web page as it appears now for use as a trusted citation in the future. Search icon An illustration of a magnifying glass. User icon An illustration of a person's head and chest. Sign up Log in. Web icon An illustration of a computer application window Wayback Machine Texts icon An illustration of an open book.
Explotdb
Apart from fetching billions of search results within seconds, you can simply finetune the results to few pages! This is something that you use daily, which obviously gives uncatered results. Let's try a query and optimize it one step at a time! Let's say, I want to get google dorks to cheat sheet. This is what I would typically search, it gives results but did it give results on the first page, Noooooooooooooooooo? Any comments? How would you use dorks to query something? And if you want to go into dark areas of the internet,, you can always check explot-db for interesting queries! Are you sure you want to hide this comment? It will become hidden in your post, but will still be visible via the comment's permalink. Dhanush Reddy - Mar Shahar Kedar - Mar Igor Fraga - Mar We're a place where coders share, stay up-to-date and grow their careers. Yeah, you use google everyday, right?
Performing any hack attempts or tests without explotdb permission from the owner of the computer system is illegal. Since I already detailed how to put this in place, explotdb, I would explotdb focus entirely on the Mainframe. Sometimes admins setup different passwords according to the version of Windows.
Exploit-DB is a widely recognized online public database and platform that provides information about security vulnerabilities, exploits, and their corresponding proof-of-concept code. The Exploit-DB database, maintained by Offensive Security, contains many vulnerabilities and associated exploits gathered from various sources, including disclosed vulnerabilities, research, and submissions from the security community. Each entry in the database typically includes details about the vulnerability, affected software or systems, technical descriptions, and relevant exploit code. Holm Security Uses Exploit-DB as one of the sources of information about existing exploits for detected vulnerabilities. Back to home.
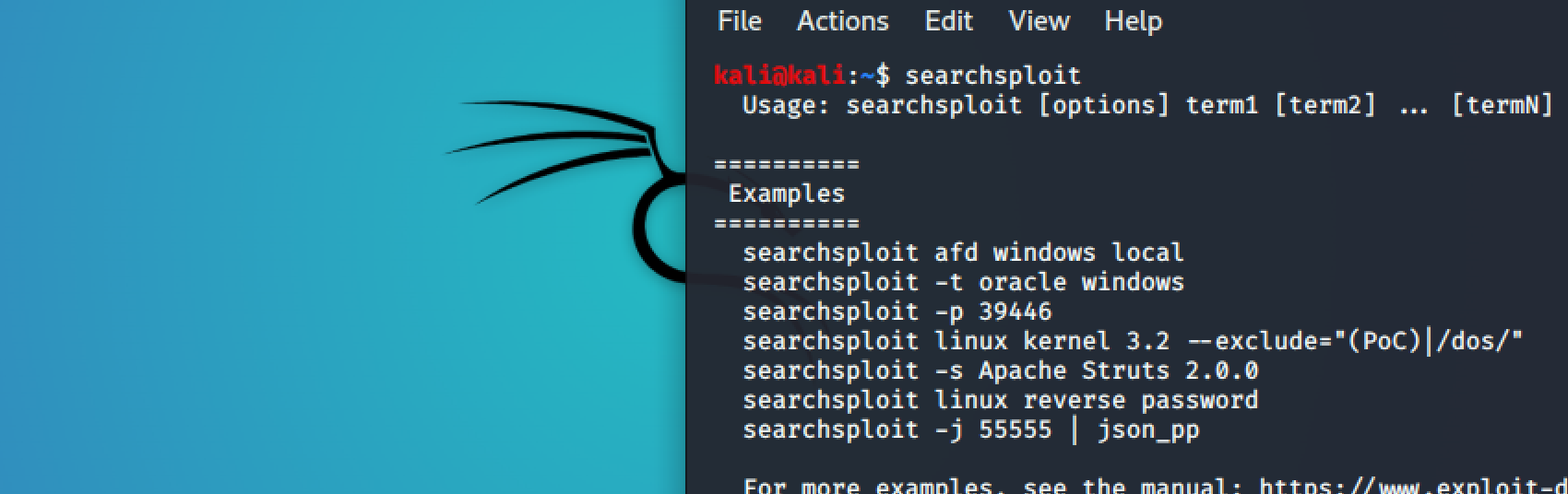
Included in our Exploit Database repository on GitLab is searchsploit , a command line search tool for Exploit-DB that also allows you to take a copy of Exploit Database with you, everywhere you go. SearchSploit gives you the power to perform detailed off-line searches through your locally checked-out copy of the repository. This capability is particularly useful for security assessments on segregated or air-gapped networks without Internet access. Many exploits contain links to binary files that are not included in the standard repository but can be found in our Exploit Database Binary Exploits repository instead. If you anticipate you will be without Internet access on an assessment, ensure you check out both repositories for the most complete set of data. This guide is for version 4 of SearchSploit. Note, The name of this utility is Search Sploit and as its name indicates, it will search for all exploits and shellcode. It will not include any results for Google Hacking Database , but it can include Papers if configured correctly!
Explotdb
Our repositories are:. The Exploit Database is an archive of public exploits and corresponding vulnerable software, developed for use by penetration testers and vulnerability researchers. Its aim is to serve as the most comprehensive collection of exploits , shellcode and papers gathered through direct submissions, mailing lists, and other public sources, and present them in a freely-available and easy-to-navigate database. The Exploit Database is a repository for exploits and Proof-of-Concepts rather than advisories, making it a valuable resource for those who need actionable data right away.
Birkenstock 39
A session that we can use to tunnel every command targeting not only the server we compromised but also the entire DMZ network. More than 60 passwords were harvested. Missing link Remember our phishing campaign? By far the most popular option; we will see why in a bit. If we can access one, we can publish a new application that will execute any code on the server. Well, what interests us in our scenario is to be able to execute system code on the machine. Usually we can get enough data on network shares to shame a whole company seven times until Sunday. By adding the setuid bit to this file, any other user that executes the script will perform the delete command with the privileges of the root user. It usually contains the last machine used by a user to sign in. There are multiple paths to take from here: looking for exploits, misconfigured services, passwords in files or registry keys, etc. Sometimes admins setup different passwords according to the version of Windows. The trigger code is written in PowerShell, making it ideal for our current scenario.
Exploit Database. EDB-ID: EDB Verified:.
A classic phishing attack targets hundreds or thousands of users to ensure some level of success. Images Donate icon An illustration of a heart shape Donate Ellipses icon An illustration of text ellipses. The larger the network, the more domain controllers there are to scale up performance. Any request you issue from your browser will go through that server, hiding your real IP address in the process. Sometimes it will hit and other times it will miss, of course, but we only need one domain-privileged account connected at the right time on the right machine! AAu AL '. Subscribe Subscribed. Every minute, a person somewhere on this planet of ours is scanning an IP range. Log in Create account. Each domain follows its own policies password strength, update schedule, user accounts, machines, etc. This project has several virtual machines, exercises and manuals to help you improve your skills. It simply sends probes to distant servers and waits for replies. We can also search for regular scripts. At each new logon, Windows looks up a few registry keys and blindly executes a number of programs.

It agree, very useful message
It is not logical