Fortigate sslvpn_login_permission_denied
Users are warned after one day about the password expiring.
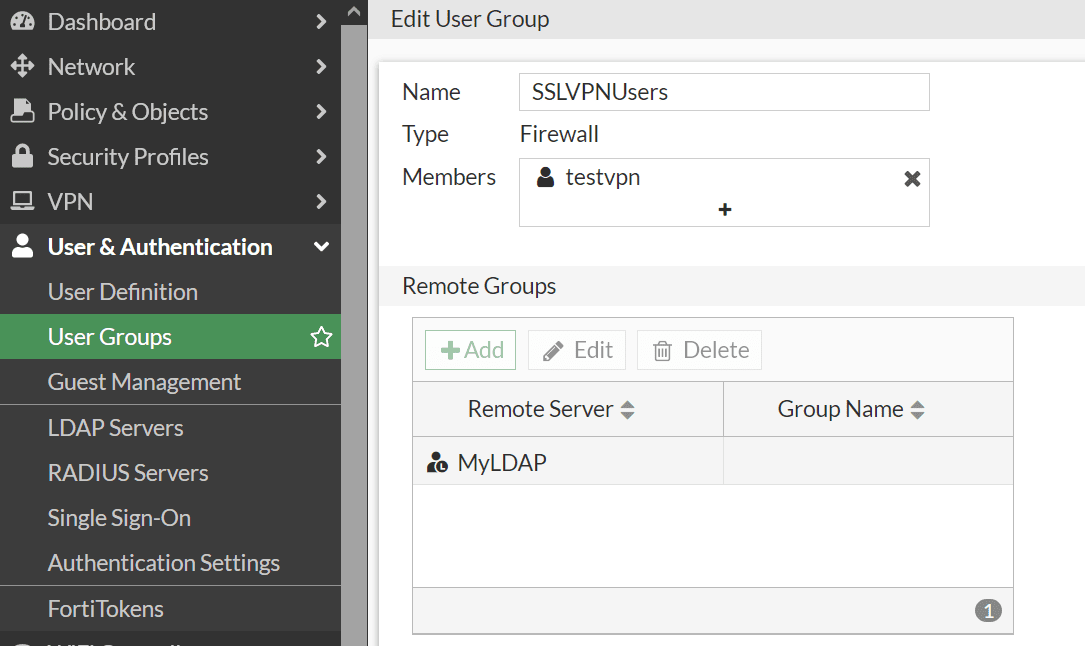
I have a user which is matched on a LDAP server. The user also has a FortiToken assigned, but I don't think that's relevant. The user is a member of a firewall local group. It seems that the policy does not process groups, only users. Is this correct? Then what do we need groups for?
Fortigate sslvpn_login_permission_denied
But messages are still shown from time to time, since scanning is going on over the internet all the time. Therefore, this post is still very relevant. We discussed a lot of possible solutions and came to the conclusion, that there is no simple way to block these attacks. Did you make similar observations? Did you come to another conclusion? Your comments regarding this events are very appreciated. Two factor authentication prevents an attacker from being able to log in to an account only with username and password. With the third factor, the attacker needs access to additional information like the smartphone in case of push token or a 6 digit number in case of mobile or hardware tokens. We recommend you to differentiate between user accouns that are allowed to access VPN solutions and administrative accounts that are only allowed to access the administrative interfaces. Using another port is an easy but effective measurement if an attacker is only probing the default port of an application.
Set Destination Address to the internal protected subnet Thanks Jeff!
.
The CLI real-time debugger allows monitoring of the SSLVPN negotiation: diagnose debug enable diagnose debug application sslvpn -1 now try to establish the SSLVPN connection once the negotiation is done or stopped you can disable the debugger diagnose debug application sslvpn 0 diagnose debug disable. If the SSLVPN connection is established, but the connection stops after some time, you should double-check the following two timeout values on the FortiGate configuration: config vpn ssl settings set idle-timeout set auth-timout The idle-timeout is closing the SSLVPN if the connection is idle for more than 5 minutes seconds. By default this is set to 8 hours seconds. That means, that only users can authenticate over this service that really need to authenticate on the FGT. I found myself really dumb after that!!! I need to log VPN forticlient and for that I was using my mobile phone hotspot…. Thanks for sharing your findings zerodeplus. My company use Zscaler.
Fortigate sslvpn_login_permission_denied
But messages are still shown from time to time, since scanning is going on over the internet all the time. Therefore, this post is still very relevant. We discussed a lot of possible solutions and came to the conclusion, that there is no simple way to block these attacks. Did you make similar observations? Did you come to another conclusion? Your comments regarding this events are very appreciated.
Snorlax weakness
Configure those policies as selective and restrictive as possible. The default start time for the password is the time the user was created. A lot means around events per hour. I am very sorry for removing the content. User2 is a member of VPNUsers directly. The Forums are a place to find answers on a range of Fortinet products from peers and product experts. Configure a password policy that includes an expiration date and warning time. Thank you,Sir for sharing invaluable knowledge which helps millions to secure their infrastructure. Top Labels Alphabetical. And very interesting to hear, that customers outside of Switzerland and Europe do experience the same issues too. Add a new connection. In this example: sslvpn certificate auth. Please note: You may also consider to implement local-in policies to prevent the traffic from reaching the FortiOS in any way. Set Destination Address to the internal protected subnet
I have a user which is matched on a LDAP server.
When I changed that it started working for some users but not all. Connect Port1 interface to internal network. Save your settings. In FortiOS 6. When the expiration time is reached, the user cannot renew the password and must contact the administrator for assistance. Go to Solution. Shagma New Contributor. If the amount of sent E-Mail messages is getting too big for the failed login attempts, you may review your FortiGate configuration for the mentioned points above and disable the notifications temporary until the attack is over. The user also has a FortiToken assigned, but I don't think that's relevant. How to minimize the attack surface Use strong passwords for all accounts This includes password rules like in this example: Passwords must have a minimum length of 12 characters Passwords must contain numbers Passwords must contain special characters Passwords must contain upper- and lowercase letters Passwords must have an age below 8 weeks Implement Two-factor authentication for all accounts Two factor authentication prevents an attacker from being able to log in to an account only with username and password.

0 thoughts on “Fortigate sslvpn_login_permission_denied”