Fortigate syslog cli
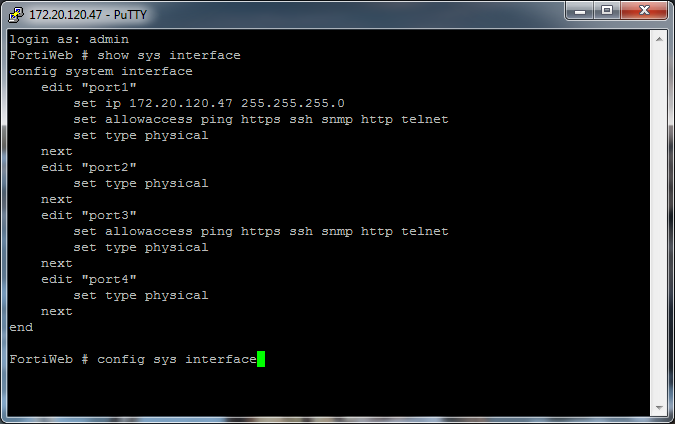
When setting with CLI, set in config log syslogd settingconfig log syslogd2 settingconfig log syslogd3 settingor config log syslogd4 setting.
Option Description enable. Log to remote syslog server. Do not log to remote syslog server. Address of remote syslog server. Maximum length:
Fortigate syslog cli
When it comes to maintaining the security and integrity of your network, checking the syslog configuration in Fortigate Firewall CLI is essential. Syslog is a protocol that allows devices to send event messages across IP networks, providing valuable information for troubleshooting and monitoring purposes. By understanding how to check syslog configuration in Fortigate Firewall CLI, you can ensure that your firewall is correctly set up to capture and transmit syslog messages, giving you insight into potential security threats and system issues. The process of checking the syslog configuration in Fortigate Firewall CLI involves accessing the command-line interface of the firewall and using commands to view and verify the syslog settings. This includes checking the destination IP address and port number where the syslog messages are being sent, as well as ensuring that the correct logging level is set to capture the desired events. By regularly reviewing and confirming the syslog configuration, you can be confident that your Fortigate Firewall is effectively monitoring and reporting on network activities, helping you maintain a secure and reliable network environment. The syslog configuration in a Fortigate Firewall CLI plays a crucial role in ensuring the security and reliability of network infrastructure. Syslog is a standard protocol that allows network devices to send event messages to a centralized server, known as a syslog server. By monitoring these syslog messages, network administrators can gain valuable insights into the health, performance, and security of their network. Checking the syslog configuration in a Fortigate Firewall CLI is essential for troubleshooting network issues, identifying security breaches, and maintaining compliance with industry regulations. This article will guide you through the process of checking and verifying the syslog configuration in a Fortigate Firewall CLI, providing step-by-step instructions and explanations. By understanding how to check the syslog configuration in a Fortigate Firewall CLI, network administrators can ensure that their firewall is properly logging events and sending them to the intended syslog server. This knowledge empowers them to detect and respond to security threats, monitor network performance, and maintain a secure and reliable infrastructure.
All Rights Reserved.
I am using one free syslog application , I want to forward this logs to the syslog server how can I do that. Go to Solution. If you configure the syslog you have to:. The important point is the facility and severity which means loca7 means "warning" not a lot of messages. If you look to the filter which is used on the FGT 5. To get really logging information of the FGT on a sylsog server both must be set to "information" which means:.
We recommend sending FortiGate logs to a FortiAnalyzer as it produces great reports and great, usable information. However sometimes, you need to send logs to other platforms such as SIEMs. You may want to filter some logs from being sent to a particular syslog server. I am going to install syslog-ng on a CentOS 7 in my lab. I always deploy the minimum install. This will be a brief install and not a lot of customization.
Fortigate syslog cli
The following list of the various test log entries output may vary depending on the FortiOS version :. FGT execute log filter category Available categories: 0: traffic 1: event 2: utm-virus 3: utm-webfilte r 4: utm-ips 5: utm-emailfilter 7: anomaly 8: voip 9: utm-dlp utm-app-ctrl utm-waf dns. The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges. Fortinet Community. Help Sign In. FortiGate Next Generation Firewall utilizes purpose-built security processors and threat intelligence security services from FortiGuard labs to deliver top-rated protection and high performance, including encrypted traffic. Article Id Technical Tip: How to perform a syslog and log test on a FortiGate with the 'diagnose log test' command. Scope FortiGate.
Sun and moon drawing
If I understand you correctly you have a free syslog server application like Kiwi and want to send logs from your Fortigate to it? Support Forum. Security Policy In Network Security. Enable syslogging over UDP. Check that the firewall has network access to the syslog server and that the syslog server is properly configured to receive messages from the firewall. Search our store. If you are not seeing any syslog messages, verify the connectivity between the Fortigate Firewall and the syslog server. By regularly reviewing and confirming the syslog configuration, you can be confident that your Fortigate Firewall is effectively monitoring and reporting on network activities, helping you maintain a secure and reliable network environment. FortiGateE 1 set logtraffic all Log all sessions accepted or denied by this policy. This can be useful for reducing the volume of logs and focusing on specific events of interest.
Logs are set to be stored on the Disk, Local Reports are disabled, logs are not sent to FortiAnalyzer, and logs are sent to my customers FortiCloud account but I cannot find any documention that would say that sending them to FortiCloud would prevent them from being sent to a syslog server.
This article will guide you through the process of checking and verifying the syslog configuration in a Fortigate Firewall CLI, providing step-by-step instructions and explanations. Fortinet Community. Log alert. I am using one free syslog application , I want to forward this logs to the syslog server how can I do that. In this section, we will address some commonly asked questions about how to check syslog configuration in Fortigate Firewall CLI. NTP daemon. Minimum value: 0 Maximum value: Each filter has a unique ID, and you can review the settings for each filter to determine which log messages are being filtered. Field custom name. User Count. Reserved for local use. Set status to enable and set server to the IP of your syslog server. We will send you an email to reset your password. Additionally, regularly reviewing and updating the syslog configuration will help in troubleshooting network issues and maintaining the security and stability of the network infrastructure. Monitoring and analyzing syslog messages can provide valuable insights into the security and performance of your network.

I think, that you are mistaken. Write to me in PM.
The authoritative answer, curiously...
I well understand it. I can help with the question decision. Together we can come to a right answer.