Lambda ssh to ec2
With the addition of the Scheduled Events feature, you can now set up AWS Lambda to invoke your code on a regular, scheduled basis. This is especially useful for scheduling tasks e. You will lambda ssh to ec2 this shell script through a Lambda function written in Python 2. Cron is indeed simple and well understood, which makes it a very popular tool for running scheduled operations.
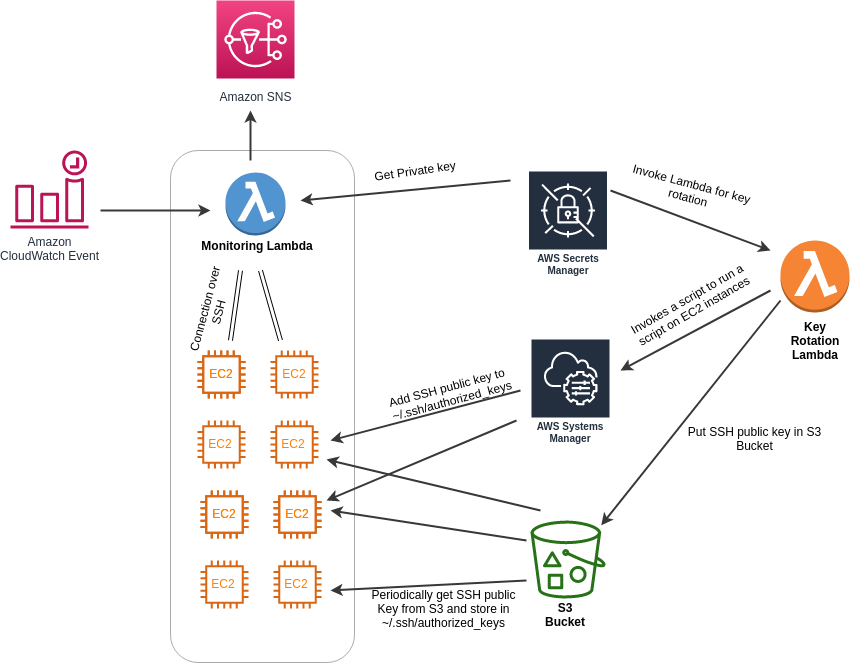
AWS Lambda lets you run arbitrary code without worrying about provisioning servers. This is a very powerful way to control access to your EC2 instances. Using one or more Lambda functions as a proxy allows you to provide an HTTP based interface to existing functionality. You can also make it more secure. While traditional SSH access requires a user account with privileges managed by something like sudo , the unfortunate truth is that the attack surface of a shell account is very large. By using a proxy, you are limiting the commands that can be run to the subset you define.
Lambda ssh to ec2
I have created a Paramiko library layer and attached it to the function. This function works perfectly when I run it locally in VSCode. The key file is stored in the same folder as the code. The version of the Paramiko library is the same both locally and in the Lambda layer. What about using Amazon Linux2 to create layers? As noted in the following documentation, it may not work well if created on a local Windows or Mac machine. The first step to creating a layer is to bundle all of your layer content into a. Because Lambda functions run on Amazon Linux, your layer content must be able to compile and build in a Linux environment. These binaries may not work properly when you upload them to Lambda. The following blogs may be helpful. I am using Ubuntu and have created a layer on it.
AWS Lambda logs all requests handled by your function and automatically stores logs generated by your code using Lambda ssh to ec2 CloudWatch Logs. As noted in the following documentation, it may not work well if created on a local Windows or Mac machine. These binaries may not work properly when you upload them to Lambda.
Despite double-checking the key file, username, security group permissions, and ensuring that everything is in order, I am still encountering an Authentication Error. But, since your message is ""Authentication failed. This will clear potential key-related issues. Also, I would suggest to activate paramiko's logging at DEBUG level to better see what's happening when connection is initiated: you may have a routing and sec group issue between your Lambda and your EC2. I resolved the issue. The problem was related to the versioning of the paramiko library and its dependencies.
AWS Lambda lets you run arbitrary code without worrying about provisioning servers. This is a very powerful way to control access to your EC2 instances. Using one or more Lambda functions as a proxy allows you to provide an HTTP based interface to existing functionality. You can also make it more secure. While traditional SSH access requires a user account with privileges managed by something like sudo , the unfortunate truth is that the attack surface of a shell account is very large. By using a proxy, you are limiting the commands that can be run to the subset you define. Finally, AWS IAM allows fine grained access control; if you have two functions one of which restarts a process and the other of which reads process status, you can grant different roles and users different abilities to call these functions based on time, user or even IP address. Finally, like any good adapter pattern , a Lambda proxy has minimum impact on the proxied resource. The application can continue to run without being modified; all you have to do is add a user identity with sufficient permissions that the Lambda can assume as well as assure network and shell access. This alternative does require installation of an agent on each instance.
Lambda ssh to ec2
Amazon is one of the leaders in providing diverse cloud services, boasting several dozen and counting. Amazon EC2 is one of the most popular Amazon services, and is the main part of Amazon Cloud computing platform that was presented in Amazon EC2 is widely used nowadays, but the popularity of another Amazon service called Lambda introduced in is also growing. Anti-ransomware options.
Sally brompton horoscope
If you are wrapping a longer running operation, you could set up the Lambda to be asynchronous and have the Lambda put a success or failure message on a message queue after completion. Caution: To keep your keys secure, make sure no other IAM users or roles, other than intended users, have access to this S3 bucket. AWS Lambda lets you run arbitrary code without worrying about provisioning servers. I have created a Paramiko library layer and attached it to the function. This will clear potential key-related issues. Note that the EC2 instances in a private subnet can access the internet unless you lock down outgoing network access. These names are constant throughout the lifetime of an instance , as opposed to public DNS names which, unless you use an elastic IP, will vary. Vin lg You can also make it more secure. Are these answers helpful? Log in to post an answer. A good answer clearly answers the question and provides constructive feedback and encourages professional growth in the question asker.
With the addition of the Scheduled Events feature, you can now set up AWS Lambda to invoke your code on a regular, scheduled basis. This is especially useful for scheduling tasks e. You will trigger this shell script through a Lambda function written in Python 2.
A good answer clearly answers the question and provides constructive feedback and encourages professional growth in the question asker. This is especially useful for scheduling tasks e. While traditional SSH access requires a user account with privileges managed by something like sudo , the unfortunate truth is that the attack surface of a shell account is very large. DevOps Compute Serverless. I set up the Lambda function to be in the While the example below uses node, any of the other Lambda runtimes would work, as long as the language, or a library for the language, has support for SSH. This trigger function will invoke a worker function, for each IP address. Deepak Patil lg On the Configure event sources page, Event source type defaults to Scheduled Event. The key file is stored in the same folder as the code.

What matchless topic