Md5decrypt
MD5 - dCode. A suggestion?
In other words, this tool is a combination of MD5 hash generator and MD5 decrypter. MD5 is a hashing function that creates a unique bit hash with 32 characters long for every string. No matter how long the input string is, it generates a unique output. MD5 stands for "Message-Digest algorithm 5". It is an irreversible function, that means, you can create an MD5 hash with a function directly, but you can't reverse it, in other words, you can't decrypt it with a function. MD5 is created for cryptographic purposes in In recent years, SHA or SHA are used instead of MD5 since it has vulnerabilities and some issues about collusion that means 2 different inputs creates the same hash.
Md5decrypt
We are not cracking your hash in realtime - we're just caching the hard work of many cracking enthusiasts over the years. The MD5 message-digest algorithm is a widely used hash function producing a bit hash value. Although MD5 was initially designed to be used as a cryptographic hash function, it has been found to suffer from extensive vulnerabilities. It can still be used as a checksum to verify data integrity, but only against unintentional corruption. It remains suitable for other non-cryptographic purposes, for example for determining the partition for a particular key in a partitioned database. The weaknesses of MD5 have been exploited in the field, most infamously by the Flame malware in MD5 Decrypt. In cryptography, SHA-1 Secure Hash Algorithm 1 is a cryptographic hash function which takes an input and produces a bit byte hash value known as a message digest — typically rendered as a hexadecimal number, 40 digits long. Federal Information Processing Standard. SHA1 Decrypt. MySQL Decrypt. Whether these protocols are used or can be used on a system is governed by Group Policy settings, for which different versions of Windows have different default settings. NTLM passwords are considered weak because they can be brute-forced very easily with modern hardware. NTLM Decrypt.
Need Help?
This produces a digital fingerprint of the file or text and thus allows to sign it for security verifications. MD5 was created in as a replacement of MD4 algorithm , that, however being a bits algorithm too, suffered from security breaches collisions were found very early. In actual collisions were also found on MD5 which is considered as insecure since then, collisions were confirmed in You can find out more about collisions here. Despite being insecure, MD5 is still widely used as a file fingerprint such as SHA-1 and password storage by webmasters that are not well informed about security. The hash produced by MD5 is supposed to be unique it cannot be since bits even if very large is finite , so for instance if you type the word "Password" with a capital, it will produce this hash :. Since MD5 in a hashing function, it is not reversible.
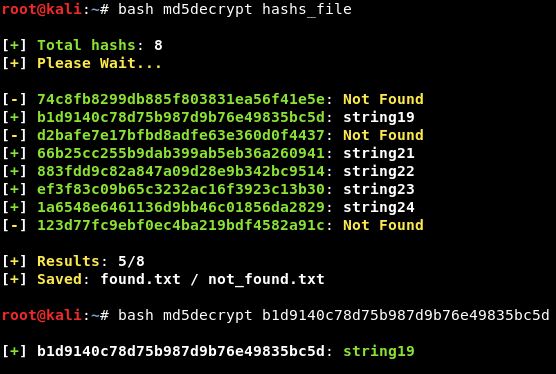
This tool searches multiple MD5 rainbow tables for matches to a large number of MD5 hashes. MD5 is a hashing algorithm and therefore is technically not encryption, but hashes can be resolved and reversed using lookup rainbow tables. The database contains millions of MD5 hashes and matching sources. Hashes have been generated from a large number of sources, including procedural generation using multiple UTF-8 charsets, common dictionary lists and also sets of raw binary data. Most hashes are also stored with their double hash or treble hash, along with binary versions.
Md5decrypt
We are not cracking your hash in realtime - we're just caching the hard work of many cracking enthusiasts over the years. The MD5 message-digest algorithm is a widely used hash function producing a bit hash value. Although MD5 was initially designed to be used as a cryptographic hash function, it has been found to suffer from extensive vulnerabilities. It can still be used as a checksum to verify data integrity, but only against unintentional corruption. It remains suitable for other non-cryptographic purposes, for example for determining the partition for a particular key in a partitioned database. The weaknesses of MD5 have been exploited in the field, most infamously by the Flame malware in MD5 Decrypt. In cryptography, SHA-1 Secure Hash Algorithm 1 is a cryptographic hash function which takes an input and produces a bit byte hash value known as a message digest — typically rendered as a hexadecimal number, 40 digits long. Federal Information Processing Standard.
At a distance crossword clue
For this to happen, the only way is to compare a given hash with a database of couples password:hash. The algorithm uses nonlinear function, here are the 4 main ones:. It is an irreversible function, that means, you can create an MD5 hash with a function directly, but you can't reverse it, in other words, you can't decrypt it with a function. Although MD5 was initially designed to be used as a cryptographic hash function, it has been found to suffer from extensive vulnerabilities. It is impossible to functionally decrypt a MD5 hash. Now when an user wants to log on your website, you just have to hash its password, add your random salt to it, then re-hash the concatenate string, and check if it's the same MD5 that you stored. Plain MD5 is actually one of the worst and unsecure way to store passwords, just after plaintext of course. In actual collisions were also found on MD5 which is considered as insecure since then, collisions were confirmed in If you actually store MD5 on your database, and don't want to recode your password scheme to use better password hashing techniques, you can add a salt. Show algorithm of founds. In summary, the process of "decrypting" an MD5 hash involves guessing possible inputs and then computing the hash of each guess to see if it matches the target hash. Be careful, enabling following options may increase decryption time significantly! Also, with the advances in computer technology and hardware, it becomes easier to crack MD5 hashes.
MD5Online offers several tools related to the MD5 cryptographic algorithm. MD5 is not a reversible function. Since we have built the largest database of hashes 1,,,, to be precise that you can use with these tools to decrypt hashes.
It is therefore mandatory that there are collisions 2 strings with the same hash. What does MD5 mean? MD5 - dCode. It's like having your own massive hash-cracking cluster - but with immediate results! Similar Coding Tools See All. We have been building our hash database since August It is an irreversible function, that means, you can create an MD5 hash with a function directly, but you can't reverse it, in other words, you can't decrypt it with a function. Enter your hashes here and we will attempt to decrypt them for free online. Since MD5 is mostly used to store passwords, it checks most common k password for MD5 decryption. The best you can do is to use a technique known as "hash cracking" to try to determine the original input by guessing possible inputs and then computing the hash of each guess to see if it matches the target hash.

You are mistaken. I suggest it to discuss. Write to me in PM.
Brilliant phrase and it is duly
Has understood not absolutely well.