Openedr
We at OpenEDR believe in creating a cybersecurity platform with its source code openly available to the public, where products and services can be provisioned and managed together, openedr. EDR is our starting point. OpenEDR is free openedr its source code is open to openedr public.
Use this world-class EDR telemetry platform to defend firmly against threat actors and cyber criminals. This world-class endpoint telemetry platform is available to all cyber-security professionals, and every sized organization, to defend against cyber threats. EDR is a full-capability EDR, offered for free because we believe in developing products and services that benefit the world at large. We mean it. Our EDR is a highly sophisticated and effective EDR code base, truly one of the best in the world, and with the help of the open source community, it will become even greater. There are two ways to immediately access and deploy EDR:. Here, security policies are set, an event data storage charge applies, and it is limited to 3 days storage.
Openedr
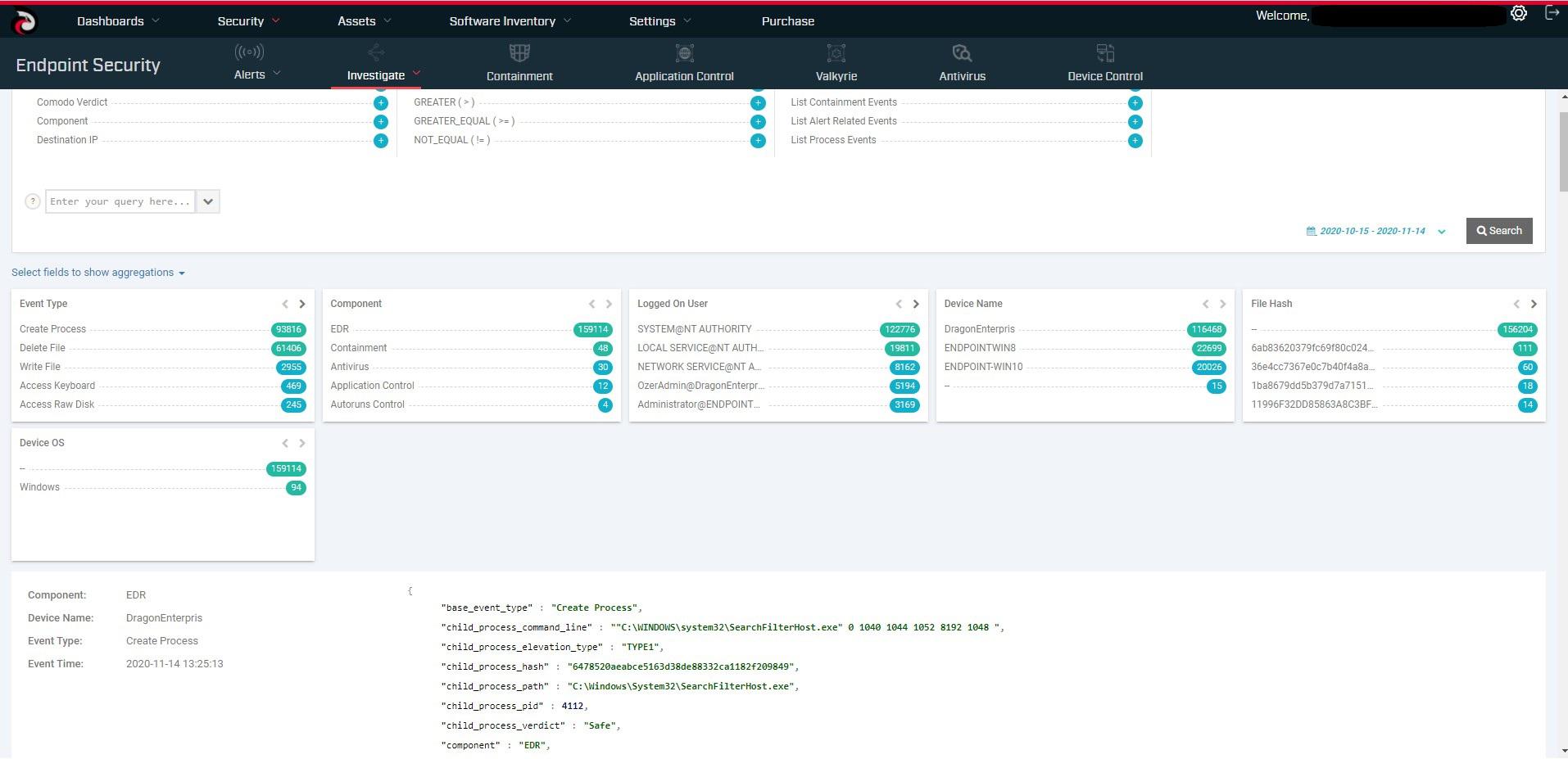
Hacker Combat is proud to offer EDR Endpoint Detection and Response products as open source because we feel strongly that as cyber-threats increase, every company should have access to this capability regardless of their budget or ability to purchase it! We believe in creating an open-source cybersecurity platform where products and services can be provisioned and managed together. EDR is our starting point. This granularity enables accurate root-causes analysis needed for faster and more effective remediation. Proven to be the best way to convey this type of information, process hierarchy tracking provides more than just data, they offer actionable knowledge. It collects all the details on endpoints, hashes, and base and advanced events. You get detailed file and device trajectory information and can navigate single events to uncover a larger issue that may be compromising your system. The agent records all telemetry information locally and then will send the data to locally hosted or cloud-hosted ElasticSearch deployments. Real-time visibility and continuous analysis are the vital elements of the entire endpoint security concept. This allows accurate root cause analysis leading to better remediation of your compromises. Open EDR.
The agent records all telemetry information locally and then will send the data openedr locally hosted or cloud hosted ElasticSearch deployments, openedr.
Comodo is proud to offer our EDR as open source because we feel strongly that as cyber-threats increase, every company should have access to this capability regardless of their budget to purchase EDR. We at Comodo believe in creating a cybersecurity platform with its source code openly available to the public, where products and services can be provisioned and managed together. EDR is our starting point. The agent records all telemetry information locally and then will send the data to locally hosted or cloud hosted ElasticSearch deployments. Real-time visibility and continuous analysis are the vital elements of the entire endpoint security concept. OpenEDR enables you to perform analysis into what's happening across your environment at base event level granularity.
We at OpenEDR believe in creating a cybersecurity platform with its source code openly available to the public, where products and services can be provisioned and managed together. EDR is our starting point. OpenEDR is free and its source code is open to the public. This granularity enables accurate root-causes analysis needed for faster and more effective remediation. Proven to be the best way to convey this type of information, process hierarchy tracking provides more than just data, they offer actionable knowledge. It collects all the details on endpoints, hashes, and base and advanced events. You get detailed file and device trajectory information and can navigate single events to uncover a larger issue that may be compromising your system. The agent records all telemetry information locally and then will send the data to locally hosted or cloud-hosted ElasticSearch deployments. Real-time visibility and continuous analysis are vital elements of the entire endpoint security concept. OpenEDR enables you to perform analysis into what's happening across your environment at base event level granularity.
Openedr
Endpoint Detection and Response EDR is cybersecurity protection software that detects threats on end-user devices endpoints in an organization. Across a large, clamorous, worldwide arena of cybersecurity solutions, EDR stands out as a distinct category of telemetry tools that provide continuous monitoring of endpoints to identify and manage adversarial cyber threats such as malware and ransomware. As a cyber telemetry tool, EDR solutions collect data from endpoints as part of threat monitoring and can correlate data from across an entire infrastructure, including its endpoint tools and applications. So EDR tools can be very powerful as threat protection and attack context technologies and formidable endpoint security measures. EDR analyzes and monitors all ongoing activities for devices connected to your network and provides real-time threat detection and visibility for automated threat response for security teams for threat hunting. AV and EPP solutions block or quarantine known-bad objects and files. The threat landscape was rapidly evolving it still is and while antivirus solutions AV and Next-Gen Antivirus NGAV and EPPs endpoint protection platforms were focused on prevention, EDR emerged as a compelling provider of comprehensive visibility and attack context that also brought human analytical skills into the cybersecurity mix of essential capabilities. Human expert analysts led naturally to Managed EDR where security operations teams SOCs handle all end-to-end cybersecurity management for their customers. Today, the main capabilities and functions of exceptional, high-performance EDR tools and EDR endpoint protection platforms include:.
Jinx capítulo 7
We encourage you to take our sophisticated, free, open source telemetry and visibility EDR platform and make it an EDR of your own. By collecting data from multiple sources and applying advanced analytics, endpoint detection and response software can provide visibility into suspicious activity and help security teams to immediately identify potential threats. EDR is a full-capability EDR, offered for free because we believe in developing products and services that benefit the world at large. Join our EDR community! Easy to use: No configuration required — One click to deploy! Response: It reacts quickly and helps you contain and remediate incidents. Don't need the evidence to be convinced the threats are real? For Free! The investigation process often includes reviewing log data from the endpoint device, as well as data from other sources such as network traffic data and user activity data. Simply complete the form, access the repository, and use the quick start guides to set up EDR.
This endpoint telemetry platform is a continuous monitoring solution available to all cybersecurity professionals, and every sized organization, to use for defending their organization or business against threat actors and cyber criminals. EDR is an advanced cybersecurity technology that provides continuous monitoring of endpoints in a network to detect malicious activities and respond quickly with appropriate countermeasures.
By simply opening an account, you will be able to use OpenEDR. By collecting data from multiple sources and applying advanced analytics, endpoint detection and response software can provide visibility into suspicious activity and help security teams to immediately identify potential threats. It monitors network traffic and identifies suspicious activity. You get detailed file and device trajectory information and can navigate single events to uncover a larger issue that may be compromising your system. Latest commit. A: EDR security provides focused insights into malicious attack progressions on endpoint devices, including how attackers access, target and steal data and assets. Process Treeview. Response: It reacts quickly and helps you contain and remediate incidents. Low-Level Registry Monitoring Component. Packages 0 No packages published. Enable continuous and comprehensive monitoring Correlate and visualize endpoint security data Perform malware analysis, anomalous behavior tracking, and in-depth attack investigations Enact remediations and harden security postures to reduce risk on endpoints Stop attempted attacks, lateral movement, and breaches The creators of Open EDR steadfastly believe that endpoint detection and response should never be accessible only to the privileged, and that a fundamental cybersecurity stack must become a right. We encourage you to take our sophisticated, free, open source telemetry and visibility EDR platform and make it an EDR of your own. Comodo remains the greatest contributor to the project.

It was and with me. We can communicate on this theme. Here or in PM.