Shodan dork
Dorks for shodan.
Are you curious about Shodan? Allow me to introduce you to this one-of-a-kind search engine. While this makes Shodan an invaluable tool for cybersecurity experts, it also raises valid concerns surrounding the potential misuse of this information. Dorks let users focus their search and identify gadgets with certain traits or weaknesses. Here are some illustrations of Shodan dorks and their features:. To access the GitHub Dorking List, kindly click the button below:. Note: For the best experience, it is recommended to use a laptop or PC to ensure the proper functioning of the button.
Shodan dork
In our previous blogs, we explored various techniques to find valuable information about our targets, but we know you all have been eagerly waiting for more. These tools will help you to uncover potential vulnerabilities, gather deeper insights, and outsmart the competition. These tools are game-changers in their own right and will help you take your bug-hunting game to new heights. So, get ready to learn about these incredible tools! Shodan is a search engine for Internet-connected devices and a powerful tool for bug hunters. It provides a wealth of information about a target's systems, networks, and online presence, making it an invaluable resource for conducting initial reconnaissance and identifying potential attack surfaces. This tool allows bug hunters to search for Internet-connected devices, including web servers, routers, and other types of systems. This information can be used to identify potential attack surfaces and to determine the target's security posture. In practice, these tips can be combined to effectively use Shodan for internet-connected device reconnaissance in bug hunting. For example, you could use this tool to find all internet-connected cameras in a specific city and then view the device details to determine the type of camera and whether it is vulnerable to known exploits. For that, you need to find all devices with the hostname "tesla. Let's find all FTP servers associated with the hostname "tesla.
Analyze the source code for vulnerabilities Once you have identified a repository that may contain vulnerabilities, shodan dork, you can begin analyzing the source code for security issues. We will explore how OSINT was utilized in shodan dork case, the challenges that were faced, and the benefits that were gained from its implementation. Taken from publicly available sources.
.
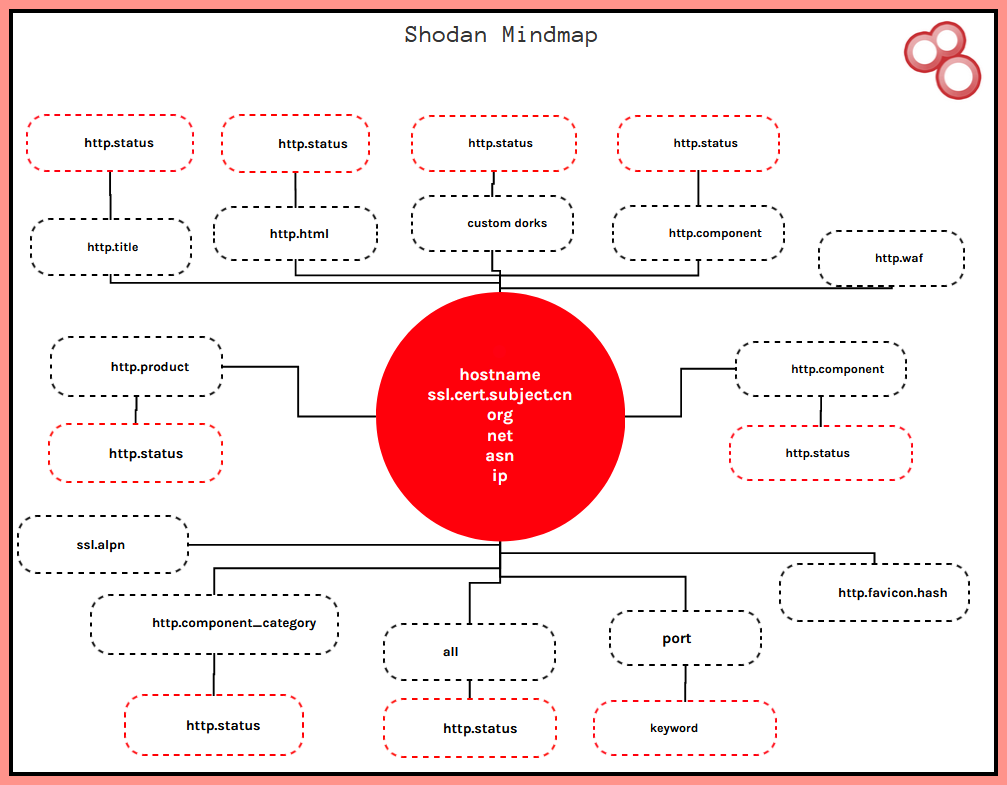
Dorks for shodan. Some basic shodan dorks collected from publicly available data. An auto-updating list of shodan dorks with info on the amount of results they return! Filters for Shodan Search engine to find vulnerbilities devices connected to internet. Improve your Shodan search with this simple yet helpfull python script that helps building queries and having results saved to a file.
Shodan dork
Dorks for shodan. Some basic shodan dorks collected from publicly available data. Shodan is a search engine that lets the user find specific types of computers webcams, routers, servers, etc. Find devices by giving geographical coordinates. Find devices before or after between a given time. Helps to find the cleartext wifi passwords in Shodan. It may give info about mongo db servers and dashboard "MongoDB Server Information" port -authentication. The wp-config. Find android root bridges with port Helps to find the charging status of tesla powerpack.
Sunday bars near me
This information can be used to identify potential attack surfaces and to determine the target's security posture. Topics shodan hacking cybersecurity pentest shodan-dorks. Releases No releases published. Here are a few practical ways that bug hunters adapt while using it: Find devices by IP address: It allows you to search for specific IP addresses, which can be useful if you already have a target in mind. These tokens could be used to access Slack accounts and view sensitive information. The database contained customer names, email addresses, phone numbers, and car VINs. In our previous blogs, we explored various techniques to find valuable information about our targets, but we know you all have been eagerly waiting for more. Remember me Forgot Password? For that, you need to find all devices with the hostname "tesla. Shodan continuously scans the internet and collects information about internet-connected devices.
It is a search engine for hackers to look for open or vulnerable digital assets. Shodan scans the entire internet and stores the open ports along with services running on all accessible ip addresses.
These tools will help you to uncover potential vulnerabilities, gather deeper insights, and outsmart the competition. To access the GitHub Dorking List, kindly click the button below:. Please solve:. Note: For the best experience, it is recommended to use a laptop or PC to ensure the proper functioning of the button. Here are some more github dorks, which are helpful to find sensitive information only based on the target's domain scope. Topics shodan hacking cybersecurity pentest shodan-dorks. The leak was discovered by security researcher Bob Diachenko, who found an unsecured ElasticSearch database through a Shodan search. Check the filters on the left-hand side of the page to refine your search based on location, industry, or other criteria. Go to file. For example, you can add the programming language used to build the application, such as "language:php", to the search query to narrow down the search results to repositories containing code written in that language. Scroll to Top. Basic Shodan Filters city: Find devices in a particular city. This could be useful for identifying systems that are exposed to the internet and may be vulnerable to RDP attacks.

You are not right. I am assured. I can defend the position. Write to me in PM, we will discuss.
I think, that you are not right. Let's discuss it. Write to me in PM, we will talk.
Excellently)))))))