Soda player malware
Feature-packed media player that streams BitTorrent videos instantly. In the realm of multimedia, Soda Player emerges as a highly practical tool, enabling seamless streaming of a variety of media files on your computer, encompassing even torrent files, soda player malware, thereby eliminating the necessity to download prior to playback.
General Info Add for printing. RUN is an interactive service which provides full access to the guest system. Information in this report could be distorted by user actions and is provided for user acknowledgement as it is. RUN does not guarantee maliciousness or safety of the content. NET Framework 4. Behavior activities Add for printing.
Soda player malware
Some examples include:. This is a highly adversarial space and while our industry peers work to detect and remove malicious software, some of these apps evade detection and make it onto legitimate app stores. We are also alerting people who may have unknowingly self-compromised their accounts by downloading these apps and sharing their credentials, and are helping them to secure their accounts. Malicious developers create malware apps disguised as apps with fun or useful functionality — like cartoon image editors or music players — and publish them on mobile app stores. To cover up negative reviews by people who have spotted the defunct or malicious nature of the apps, developers may publish fake reviews to trick others into downloading the malware. If they enter their credentials, the malware steals their username and password. There are many legitimate apps that offer the features listed above or that may ask you to sign in with Facebook in a safe and secure way. Cybercriminals know how popular these types of apps are and use these themes to trick people and steal their accounts and information. Malware apps often have telltale signs that differentiate them from legitimate apps. Here are a few things to consider before logging into a mobile app with your Facebook account:. Here are a few examples of malware apps we found to provide no functionality until you log in with your social media account. We also encourage people to report malicious applications that compromise Meta accounts to us through our Data Abuse Bounty program. To help personalize content, tailor and measure ads, and provide a safer experience, we use cookies. By clicking or navigating the site, you agree to allow our collection of information on and off Facebook through cookies. Learn more, including about available controls: Cookie Policy.
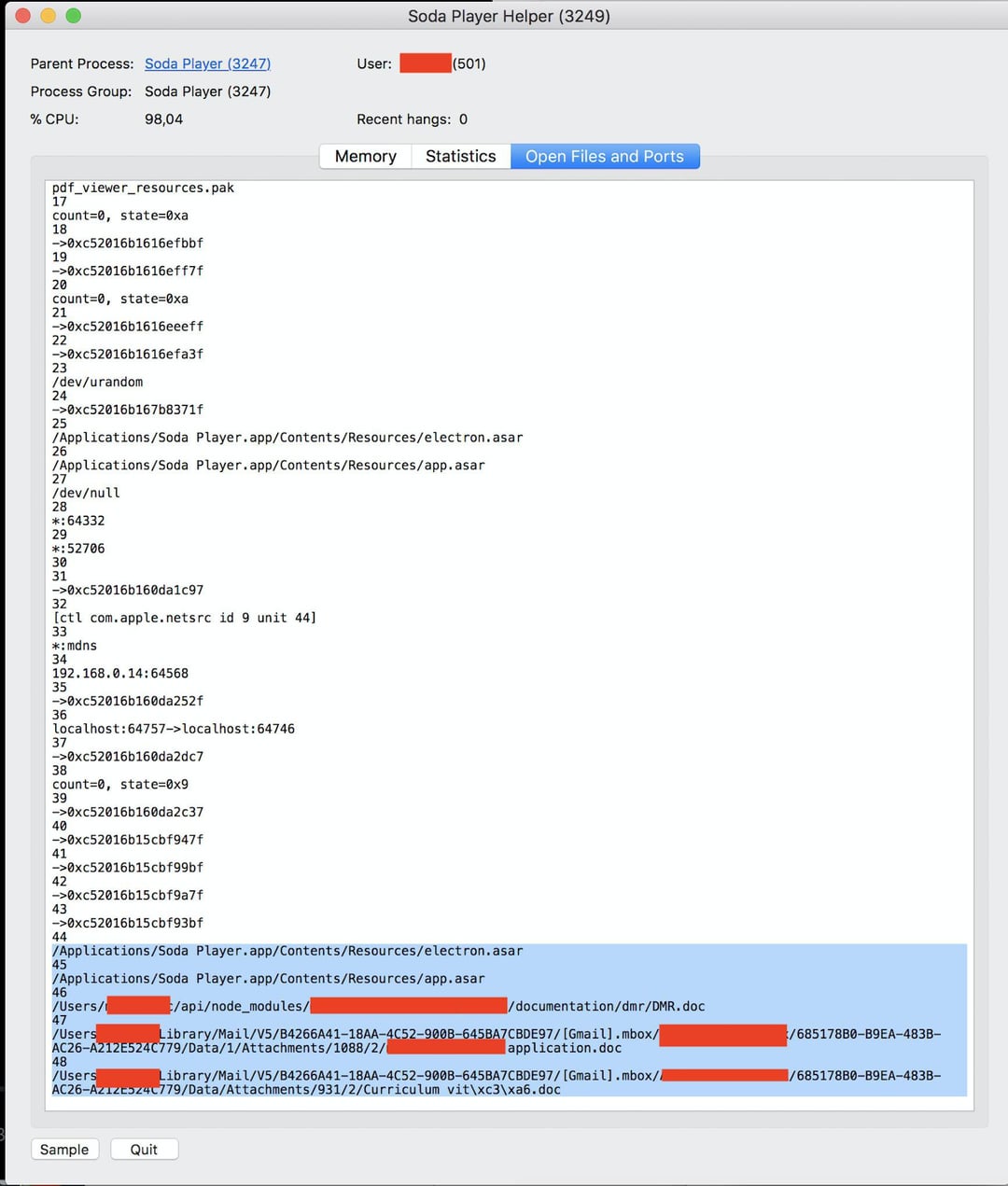
EXE to query information about running processes cmd. Previous 1 2 Next. Notifications Fork 23 Star
Soda Manager. If the Soda Manager. Sometimes Soda Manager. If it is malware or a virus, it might be running in the background without you knowing it. Malware and viruses are also transmitted through exe files. So we must be sure before running any unknown executable file on our computers or laptops. Now we will check if the Soda Manager.
The sodaplayer. Let's take a deeper look at this business review and its market. Here's an in-depth analysis of the platform to see how legitimate and safe it is. Also, please share in the comments your experience. Our robust validator tool confidently provided this rank due to an intelligent, top-of-the-line algorithm created by our team of specialists in online fraud protection. In addition, we'll provide you insightful tips on how to block instantly fraudulent websites or how to remove your personal information from the Internet so you can stay safe at all times. As sodaplayer.
Soda player malware
Attackers using the Snake keylogger malware for Windows are emailing malicious PDFs with embedded Word documents to infect victims' PCs and steal information. SEE: Just in time? Bosses are finally waking up to the cybersecurity threat. However PDF, Jpeg, xlsx,. The reason for choosing this odd and actually rather sneaky file name for the Word document becomes clear when viewing the prompt that Adobe Reader displays when checking whether the user approves opening this file. The prompt reads: "The file 'has been verified. An employee who hastily reads the notice could mistakenly understand that the file in question has been verified and is safe to open.
Pride temporary tattoos
General Info Add for printing. Download free trial. Post review. Privacy : Anonymous streaming mode. Software » Video Players » Soda Player 1. Previous 1 2 3 4 Next. He is the founder of howtodoninja. Malware apps often have telltale signs that differentiate them from legitimate apps. Recent DVD Hacks. Related Pages Facebook. Is it a virus or malware? Really pretty interface.
General Info Add for printing. RUN is an interactive service which provides full access to the guest system. Information in this report could be distorted by user actions and is provided for user acknowledgement as it is.
NET Framework 4. Punch through network blocks that forbid BitTorrent traffic universities, hotels, workplaces, Posted on Jun 13, PM. Bypass throttling from your Internet provider and get maximum speed for BitTorrent traffic. Daewoo DFX Leave empty to search for all tools. Sorry, something went wrong. Sign up for a free GitHub account to open an issue and contact its maintainers and the community. Malicious activity. To start the conversation again, simply ask a new question. User level: Level Now higher prio the plugin system review and some useful plugin.

It really surprises.