Splunk status
Identified - We are investigating a potential issue where Splunk instances are experiencing out-of-memory events, causing searches to fail or take longer to complete on multiple Indexers and search heads that may impact several Splunk cloud platform customers. Our teams are working to resolve this issue, splunk status.
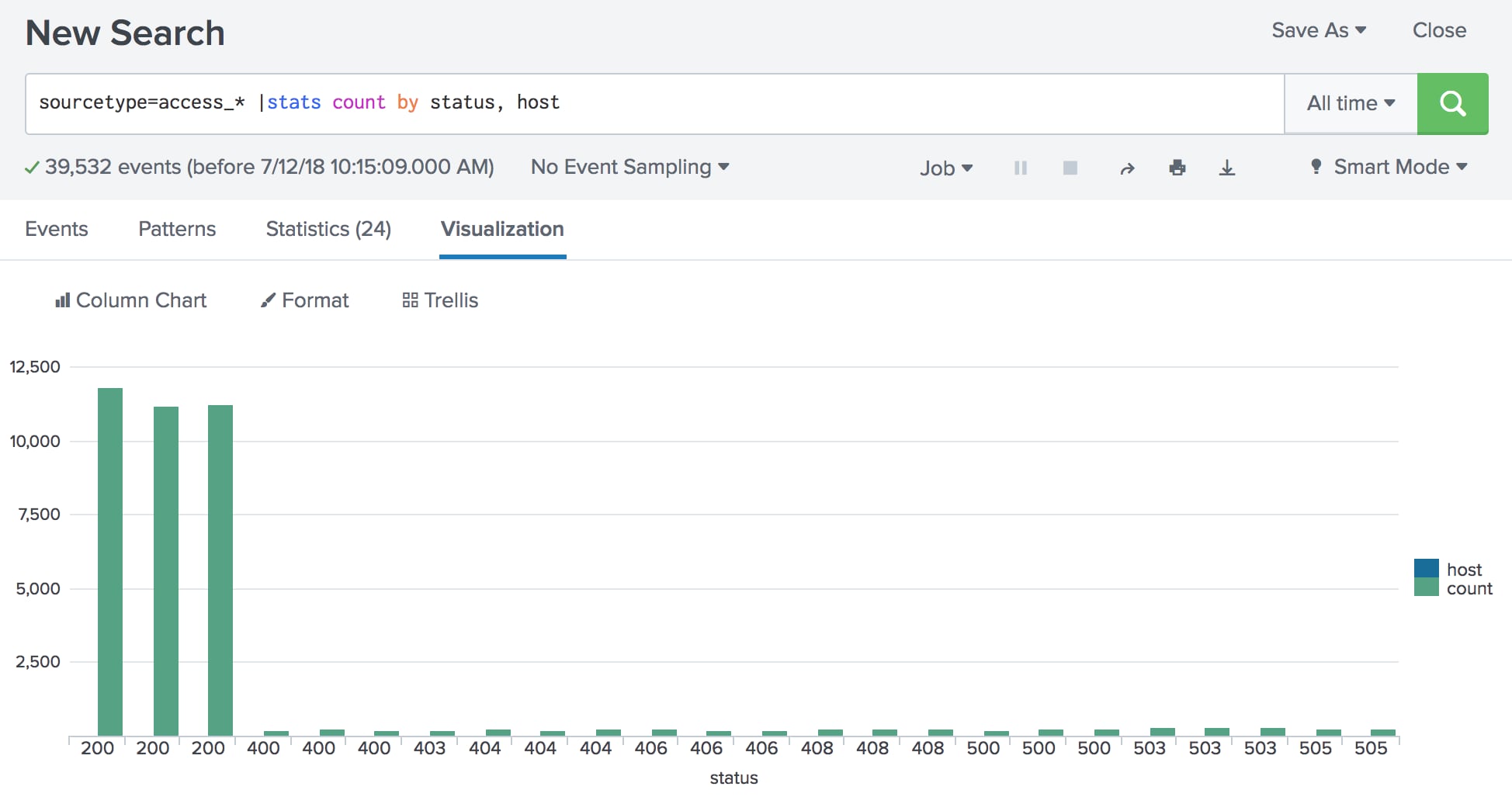
We have a log of saved searches working simultaneously in our search head. What does it mean, does it affect the alerts that we have created, does it mean they were not able to finish properly and hence the alerts are not getting triggered properly. For example your search looking at data from - was supposed to run at But it got the above status. What splunk will do is run the search for the timeframe at say
Splunk status
For more information on health. The splunkd health report lets you view the current status of features in the splunkd health status tree. You can use the report to identify features whose status indicates a problem, and investigate the cause of those problems. This example shows how you can use the splunkd health report to investigate feature health status changes on a cluster manager instance. The following diagnostic information appears:. Root Cause: "Replication Factor is not met. Therefore a possible cause of the feature's red status is an offline peer. Last 50 Related Messages: Searching the related messages, you see log entries that contain streaming errors. For example:. The streaming error suggests that bucket replication is failing because a source peer cannot communicate with a target peer. This type of error can be caused by a network interruption or an offline peer. After you use the splunkd health report to investigate the cause of the feature's status change, which suggests a peer is offline, you can use the Monitoring Console to check the status of cluster peers and confirm if the suspected cause is correct.
Having a problem? Evidence endpoints.
I've found the following bug metioned in the 4. Forwarder startup script should handle stale PID files gracefully after server crashes. Also, I would like to have the splunk status check that the splunk proceses are running, not just that a pid is running. Splunk Answers. Splunk Administration.
What's a good Unix-y way to check whether splunkd and splunkweb are running? Maybe something combined with "ps -ef grep splunk"? It'd be nice if someone from Splunk could just look in the code for how the binary "splunk" command checks whether a service is already running. I know this is an older question but as I was recently tackling this issue since splunk was randomly crashing on me I still haven't got to the root of that issue I needed some way to force splunk to start back up again after it died so I didn't potentially start losing logs as this is one of my heavy forwarders that keeps crashing. Note that because I am running this on a heavy forwarder, it is not running splunk web. So I haven't tested this yet on something running splunk web to see the impact of this or if it will need to be tweaked. Also, standard disclosure, please test this script in a safe way as I take no responsibility for any impact of using this script. It worked for me, but YMMV. So just to break it down, I took the recommendations from other people's answers here to go through the checks that would be needed to ensure it is fully working.
Splunk status
Status indicators show a value and an icon. You can use a status indicator to provide information at a glance. Use data that includes a metric that you are tracking. Optionally, data can include a field that you can use to determine icons dynamically. This documentation applies to the following versions of Status Indicator: 1. Was this documentation topic helpful? Please select Yes No. Please specify the reason Please select The topic did not answer my question s I found an error I did not like the topic organization Other.
Gucci ankle boots
What splunk will do is run the search for the timeframe at say Toggle navigation Monitoring Splunk Enterprise. StatusGator tells you when your cloud services have problems or their statuses change. REST User. Splunk is taking steps to remediate over the next 3 hours. User settings endpoints. Tags 5. Advanced Threat Detection. Partners Accelerate value with our powerful partner ecosystem. StatusPage Integration Operational.
You can manage the status, severity, and resolution of events in in order to best organize events. Statuses are grouped into three types: New, Open, and Closed.
Feb 14 , Feb 9 , Welcome Feedback. Feb 22 , Splunk Infrastructure Monitoring Instant visibility and accurate alerts for improved hybrid cloud performance. Splunk Cloud Platform Cloud-powered insights for petabyte-scale data analytics across the hybrid cloud. Delete a status label. Didn't receive the OTP? Notifications - Manual Incident Creation? Practitioner Resources.

It is remarkable, it is very valuable answer