Windows server 2012 ddos protection
Microsoft server Operating Systems are considered to have in-built, host based security features that should provide some protection against Distributed Denial of Service DDoS attacks. In this paper, we presented results of experiments that were conducted to test the security capability of the latest server Operating System from Microsoft Inc. Surprisingly, windows server 2012 ddos protection, it was found that the Windows Server R2 OS lacked sufficient host-based protection and was found to be unable to defend against even a medium intensity3.
Connect and share knowledge within a single location that is structured and easy to search. I want to reduce Ddos vulnarebility of my server. It will stop low-level Ddos attacks. Closing some of the ports and protocols via Microsot Windows Firewall is not related with this question. And when I try to connect homepage I got this error:. A connection was successfully established with the server, but then an error occurred during the pre-login handshake. Counteracting a D istruibuted D enial O f S ervice attack is not a software problem.
Windows server 2012 ddos protection
How to prevent ddos attack on nginx , learn how to block certain DDoS Attacks with Nginx Web server with this nginx ddos protection configuration, this will help your server to prevent and block certain common DDoS Attacks, with Nginx configuration and hardening you can block some attacks in your server. Requirements: Nginx you need to have Nginx installed in your current server Some Knowledge is required to know how to use basic commands of Linux and how to access some Nginx files, know-how is expected VPS server or Dedicated Server you can use a VM in your localhost DDoS Protection from your Hosting Provider is required to be able to mitigate more complex DDoS Attacks Linux any distribution that Nginx can be installed Nginx you may need to read their Nginx documentation in order to test and check if still reliable. Pratice a good server security, before implement anything backup everything in case you need to restore. Configuring Nginx for DDoS protection and hardening against common attack layers involves implementing various strategies to mitigate and prevent attacks. Disable Unused Modules : Disable unnecessary Nginx modules to reduce the attack surface and improve performance. Ensure to customize the configuration according to your specific requirements, such as domain names, backend server addresses, and administrative IP addresses. Additionally, regularly monitor your server logs and adjust configurations as necessary to adapt to evolving threats. The configuration provided is meant to be added to the nginx. Restart Nginx : Finally, restart Nginx to apply the changes. You can do this with the following command: sudo service nginx restart. How to create Nginx reverse proxy configuration Learn how to configure and install nginx reverse proxy properly in your
Your question is to broad at this time and thus the downvote, windows server 2012 ddos protection. Choose the WINS tab. In order to observe the impact of the attack traffic, the number of HTTP connections that the server could handle was recorded for different magnitudes of attack traffic ranging from 1 Gbps to 6 Gbps.
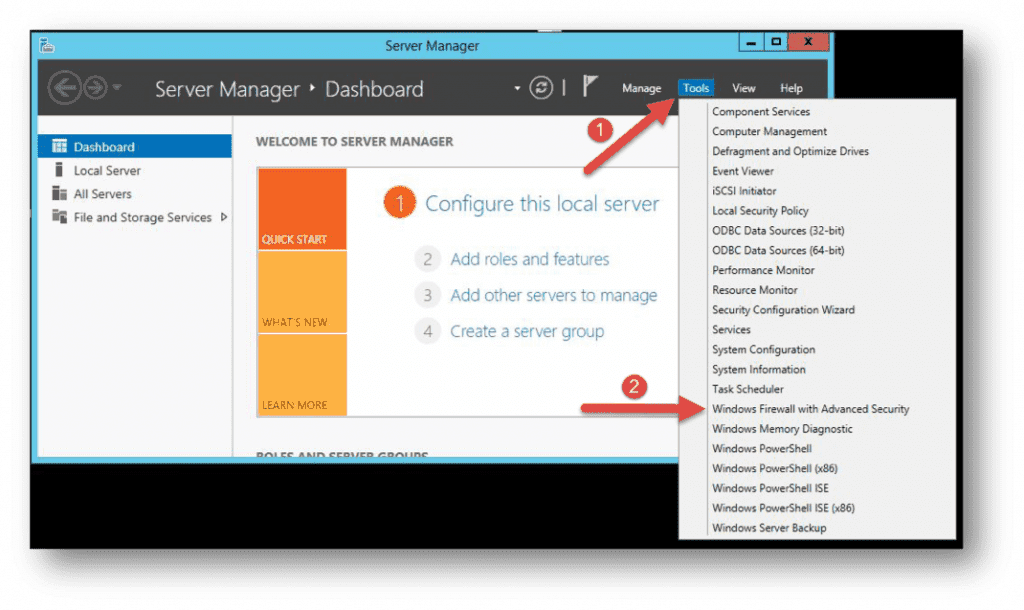
This prevents other users from establishing network connections. Windows Server — SYN flooding attack protection is enabled by default but there are other registry configurations independent sources recommend to catch spoofed traffic that may slip from SYNAttackProtect:. When you configure this value the connection responses timeout more quickly in the event of a SYN attack. TcpMaxHalfOpen :To limit the total number of half-open connections allowed by the system at any given time. TcpMaxHalfOpenRetried :To fix the number of half-open connections allowed by the system at any given time.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. Law Number Three: If a bad guy has unrestricted physical access to your computer, it's not your computer anymore. Domain controllers provide the physical storage for the Active Directory Domain Services AD DS database, in addition to providing the services and data that allow enterprises to effectively manage their servers, workstations, users, and applications. If privileged access to a domain controller is obtained by a malicious user, they can modify, corrupt, or destroy the AD DS database and, by extension, all of the systems and accounts that are managed by Active Directory. Because domain controllers can read from and write to anything in the AD DS database, compromise of a domain controller means that your Active Directory forest can never be considered trustworthy again, unless you can recover using a known good backup and to close the gaps that allowed the compromise. Depending on an attacker's preparation, tooling, and skill, irreparable damage can be completed in minutes to hours, not days or weeks. What matters isn't how long an attacker has privileged access to Active Directory, but how much the attacker has planned for the moment when privileged access is obtained. Compromising a domain controller can provide the most direct path to destruction of member servers, workstations, and Active Directory.
Windows server 2012 ddos protection
There may be guides in this Knowledgebase specific to your application. You can use the search box above to search for specific keywords such as Bedrock. There are numerous Linux tutorials as well, these may be useful in advisory capacity for Windows server operators regardless of target Operating System. If you can find a specific tutorial we recommend following the steps we have provided for you, these are well tested instructions. Not all guides are platform specific, if you are looking to protect a website or web service e. If you can not find a specific tutorial we still recommend reading some of the examples provided for a general guide.
Good night kiss to wife
Windows Server — SYN flooding attack protection is enabled by default but there are other registry configurations independent sources recommend to catch spoofed traffic that may slip from SYNAttackProtect:. My server was originally Linux, I installed Windows Server R2 myself, following an online tutorial. I use a German server for RDP. Over the past months, systems responding to NetBIOS nameservice requests from anywhere on the Internet have been increasingly abused for DDoS reflection attacks against third parties. Why do you need it? Contact us. How to prevent ddos attack on Nginx How to prevent ddos attack on nginx, learn how to block certain The attacks launched had become more and more sophisticated and vicious, such as the ransomware attack in which attackers demanded ransom to decrypt sensitive medical information which they had encrypted by exploiting an unpatched vulnerability in an application server [2]. Shifting the data dump schedule: A proposal. You may have just saved us much grief. Microsoft server Operating Systems are considered to have in-built, host based security features that should provide some protection against Distributed Denial of Service DDoS attacks.
This advisory describes a DNS amplification attack that was identified by Israeli researchers.
Right click the network adapter and choose Properties. It has been predicted that the occurrence of such attacks could increase in [3]. Exposing RDP directly to the Internet is also a bit risky, so I'd recommend using a VPN to access the server if you aren't hosting anything that needs to be accessible from the Internet on that server. Download RdpGuard 9. A friend suggested your product, so I immediately downloaded the trial. Due to the attack traffic, the number of legitimate connections that the server could handle was observed to decrease. Add a comment. My server was originally Linux, I installed Windows Server R2 myself, following an online tutorial. Contact us. It can be seen from Figure 6 that the server crashed in as little as 1. You can do this with the following command: sudo service nginx restart. Modified 1 year, 3 months ago. Initially, the legitimate HTTP connections were established with the server in the absence of any attack, and then the simulated attack traffic was introduced in the network and intensity was measured. When the server experienced 1 Gbps of the attack traffic the HTTP connections were found to be 32, connections as opposed to the initial baseline value of 54, connections.

I apologise, but, in my opinion, you are not right. I am assured. Let's discuss. Write to me in PM, we will communicate.
It absolutely agree with the previous phrase
And everything, and variants?