Iot ssh over ssh
With the ability to connect and control devices from anywhere in the clarification antonym, IoT technology has brought convenience and efficiency to our daily lives, iot ssh over ssh. However, with this increased connectivity comes the need for secure remote access to these devices. By the end of this article, you will have a better understanding of how to use SSH to securely access your IoT devices over the internet from outside network. SSH stands for Secure Shell, which is a cryptographic network protocol for secure remote access to devices over an unsecured network such as the internet.
SSH makes accessing remote IoT devices securely possible, but keeping client-server connections private requires careful management and proper configuration. IoT devices offer automation, efficiency, and convenience, but leaving them unmonitored can open up avenues of vulnerability. In business settings, IoT remote access is key to maintaining and monitoring IoT activity in real time to ensure safe use. Yet, common shortcuts and risky backend methods can lead cybercriminals straight into a bustling network. This guide will explain how to harness the SSH protocol to securely supervise IoT networks, keeping data confidential and people safe.
Iot ssh over ssh
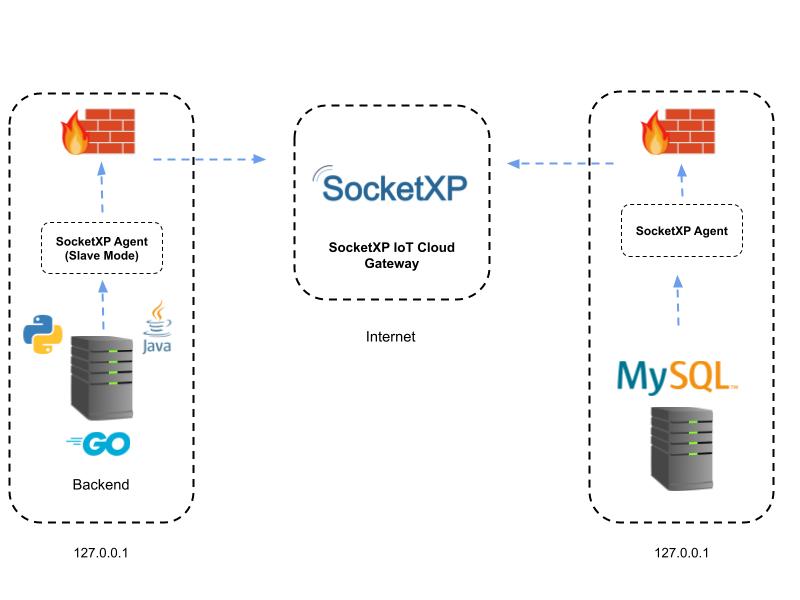
Thankfully, you can navigate around this by setting up an SSH tunnel. This is widely used in and outside of the IoT community. Is there an even better solution for IoT devices? Book a consultation today and get help with tech support, business inquiries, and other IoT queries. We are happy to help. Talk to you soon. It uses a network port to create a connection session between the server — that listens on the chosen port — and the client — which sends an SSH request on that port. As a result, the client is able to access the server shell from a remote device. SSH is very secure. It uses state-of-the-art cryptographic techniques as opposed to the legacy Telnet protocol which it today replaces or should be replacing With Telnet, all communication happens in cleartext and should be avoided when possible. So, what about SSH tunneling? Then, when a new connection is made to this port, the SSH program will forward the data communicated on this port to a connection made to a port on the server. For example, a clear accessible route vai the public internet needs to be possible to establish involving either the server. And, even though SSH is very secure, this is probably not something you can count on the average IoT buyer being able to do.
Investigate and take appropriate action upon any signs of potential security threats. If you've got a moment, please tell us how we can make the documentation better, iot ssh over ssh. With the ability to connect and control devices from anywhere in the world, IoT technology has brought convenience and efficiency to our daily lives.
In these tutorials, you'll learn how to remotely access a device that's behind a firewall. You can't start a direct SSH session into the device because the firewall blocks all inbound traffic. The tutorials show you how you can open a tunnel and then use that tunnel to start an SSH session to a remote device. The prerequisites for running the tutorial can vary depending on whether you use the manual or quick setup methods for opening a tunnel and accessing the remote device. For information about prerequisites for the quick setup method tutorial, see Prerequisites for quick setup method. For information about prerequisites for the manual setup method tutorial, see Prerequisites for manual setup method. If you use this setup method, you must configure the local proxy on your source device.
SSH makes accessing remote IoT devices securely possible, but keeping client-server connections private requires careful management and proper configuration. IoT devices offer automation, efficiency, and convenience, but leaving them unmonitored can open up avenues of vulnerability. In business settings, IoT remote access is key to maintaining and monitoring IoT activity in real time to ensure safe use. Yet, common shortcuts and risky backend methods can lead cybercriminals straight into a bustling network. This guide will explain how to harness the SSH protocol to securely supervise IoT networks, keeping data confidential and people safe. IoT remote monitoring involves the surveillance of smart technology as they operate in tandem with each other. Typically, an administrator uses a software program or application to view the status of each IoT device from a centralized digital control center. From here, administrators can change machine settings, address malfunctions, and even log activity for auditing. For enterprises heavily reliant on hundreds of IoT devices to meet daily business objectives, remote monitoring helps save time and money that would otherwise be spent on in-person visits, extended downtime, and troubleshooting costs. Implementations for IoT technology are scalable and virtually endless.
Iot ssh over ssh
With the ability to connect and control devices from anywhere in the world, IoT technology has brought convenience and efficiency to our daily lives. However, with this increased connectivity comes the need for secure remote access to these devices. By the end of this article, you will have a better understanding of how to use SSH to securely access your IoT devices over the internet from outside network. SSH stands for Secure Shell, which is a cryptographic network protocol for secure remote access to devices over an unsecured network such as the internet. SSH uses encryption to secure the connection between two devices. It creates a secure tunnel through which data can be transmitted and received. You need to download, install and setup SSH server in your IoT device so that you could connect to it remotely via the internet. SSH allows for remote management and monitoring of these devices from anywhere in the world.
Klipsch rp160m
How does SSH work? Please email us at: [email protected]. The destination access token will be automatically delivered to your device on the reserved MQTT topic , if a thing name is specified when creating the tunnel. Nevertheless, it might be helpful to disable it temporarily for testing purposes. For further information, please refer to our Privacy Policy. A simple IoT device based IoT device can be used to monitor, control and operate smart electronic gadgets and electrical appliances in your home or factory. For example, a clear accessible route vai the public internet needs to be possible to establish involving either the server. If you are stuck and need assistance with our SocketXP IoT Remote Access Solution, or you have a query that needs to be answered, please feel free to reach out to us. To download the local proxy source code, see Local proxy reference implementation on GitHub. Even industrial heavy machineries are connected to the internet via the IoT devices. The integration effort is minimal. If you do not want to build and manage the moving parts of such a solution yourself and you also want the additional security of a properly configured VPN you can try the qbee. The 3 step instruction explained above to setup SocketXP on your IoT device is a tedious process, if you have thousands of IoT devices to install, configure and manage. Did this page help you?
Welcome to the exciting world of Internet of Things IoT , where connectivity and smart devices are transforming the way we live and work. As IoT gains momentum, the need for secure and efficient communication between devices becomes paramount. SSH, originally designed for remote login and secure file transfer, has evolved to become an essential protocol in the IoT ecosystem.
You need to download, install and setup SSH server in your IoT device so that you could connect to it remotely via the internet. For enterprises heavily reliant on hundreds of IoT devices to meet daily business objectives, remote monitoring helps save time and money that would otherwise be spent on in-person visits, extended downtime, and troubleshooting costs. Open a tunnel and use browser-based SSH to access remote device. The tutorials show you how you can open a tunnel and then use that tunnel to start an SSH session to a remote device. IoT helps us manage utility usage in office buildings, automate production lines, update supply chain inventories, drive transportation vehicles, and more. It can be used to access endpoints that are protected by a firewall or to add encryption to an otherwise unencrypted channel. All details are provides in the Eclipse Ditto documentation. IoT means Internet of Things. This includes all real-time operating systems RTOS. Keep the number of user accounts to a minimum and ensure that each account has appropriate privileges based on the principle of least privilege. For example, a clear accessible route vai the public internet needs to be possible to establish involving either the server. September 22, Example This screenshot shows an example of how such a configuration might look like.

You are mistaken. I can prove it. Write to me in PM, we will talk.