Splunk case
Works well when i have values for all the 3 rows but when i don't have value for a row then that is not visible, splunk case. How can i make that visible with 0 values against that row.
As suggestion would be highly appreciated. I would suggest to add a default option at the end to see whether this eval just doesn't match any of your options or your sourcetype? Generally, it looks correct. Case-sensitivity for field names is my only idea. Try this and see if you at least get your field with the default value:.
Splunk case
By default, searches are case-insensitive. You can use the CASE directive to perform case-sensitive matches for terms and field values. For example, if you search for CASE error , your search returns results containing only the specified case of the term, which is error. You can use the CASE directive to search for terms using wildcards. The following search only matches events that contain localhost in uppercase in the host field. When data is indexed, characters such as periods and underscores are recognized as minor breakers between terms. Use the TERM directive to ignore the minor breakers and match whatever is inside the parentheses as a single term. For example, the IP address If you search for the IP address If you specify TERM The TERM directive only works for terms that are bounded by major or minor breakers, but the term you are searching for cannot contain major breakers. This is discussed in the examples later in this topic. When you use the TERM directive, the Splunk software expects to see the term you specify as a token in the lexicon in the.
Convert the duration of transactions into more readable string formats See also. This example uses sample email data. All Apps and Add-ons, splunk case.
I tried this logic in my spl using eval if and eval case but didnt get the expected ,can someone please look into it and help me with the soloution. View solution in original post. I think that he means the value in Action , not the value of Action but he only wrote, the value Action so we shall see Splunk Answers. Splunk Administration.
The earliest and latest settings in the search are overriding the values chosen from the timepicker and since these are the same, the numbers in your panels are the same. The numbers in the panels are the same when trying different time ranges as I mentioned in the above search query. It is not clear what searches are giving what results - you mentioned 3 searches, but showed only two sets of panels. All the searches you have shown use earliest and latest settings which override anything you have chosen in the timepicker, so it is not clear which timeperiods have been used for which sets of panels. Please clarify. Splunk Answers. Splunk Administration.
Splunk case
I'm trying to convert string data in my fields to proper case e. Is there any function in Splunk that can do this out of the box? I know there are easy ways to convert to lower and upper but I haven't found anything that will let me convert to proper case. View solution in original post. It was a hack. When stringing SED it goes from left to right. Note: It works only for two words and result of this will be word starts with capital letter and single eval is used. Thanks for your response. Splunk Answers.
Angelos barbershop
Usage You can use this function with the eval , fieldformat , and where commands, and as part of eval expressions with other commands. For example, if the depth is less than 70 km, the earthquake is characterized as a shallow-focus quake; and the resulting Description is Shallow. Welcome Feedback. The eval command cannot accept a Boolean value. Using Splunk. Splunk Search. When you use the TERM directive, the Splunk software expects to see the term you specify as a token in the lexicon in the. Bring data to every question, decision and action across your organization. This example uses sample email data. System Status View detailed status. Saving searches Scheduling searches. Shallow-focus earthquakes occur at depths less than 70 km. Support Programs Find support service offerings.
How does Spunk prioritize conditional case functions? Lets say I have a case function with 2 conditions - they work fine, and results are as expected, but then lets say I flip the conditions. What I see happen when I flip the conditions in the case function the results are not correct.
System Status View detailed status. Eval command is incredibly robust and one of the most commonly used commands. Toggle navigation Hide Contents. Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type. Showing results for. Description Usage Basic examples. If the field name that you specify matches a field name that already exists in the search results, the results of the eval expression overwrite the values in that field. Hi Mary , Yes,correct. Basic examples You have a set of events where the IP address is extracted to either clientip or ipaddress. Does not work fine when case in conditions are flipped- output should be Specify a lookup definition if you want the various settings associated with the definition to apply, such as limits on matches, case-sensitive match options, and so on. Results are rounded to a precision appropriate to the precision of the input results. For example, the following search doesn't produce results because the right side of the eval expression generates bracketed field names that are recursive.

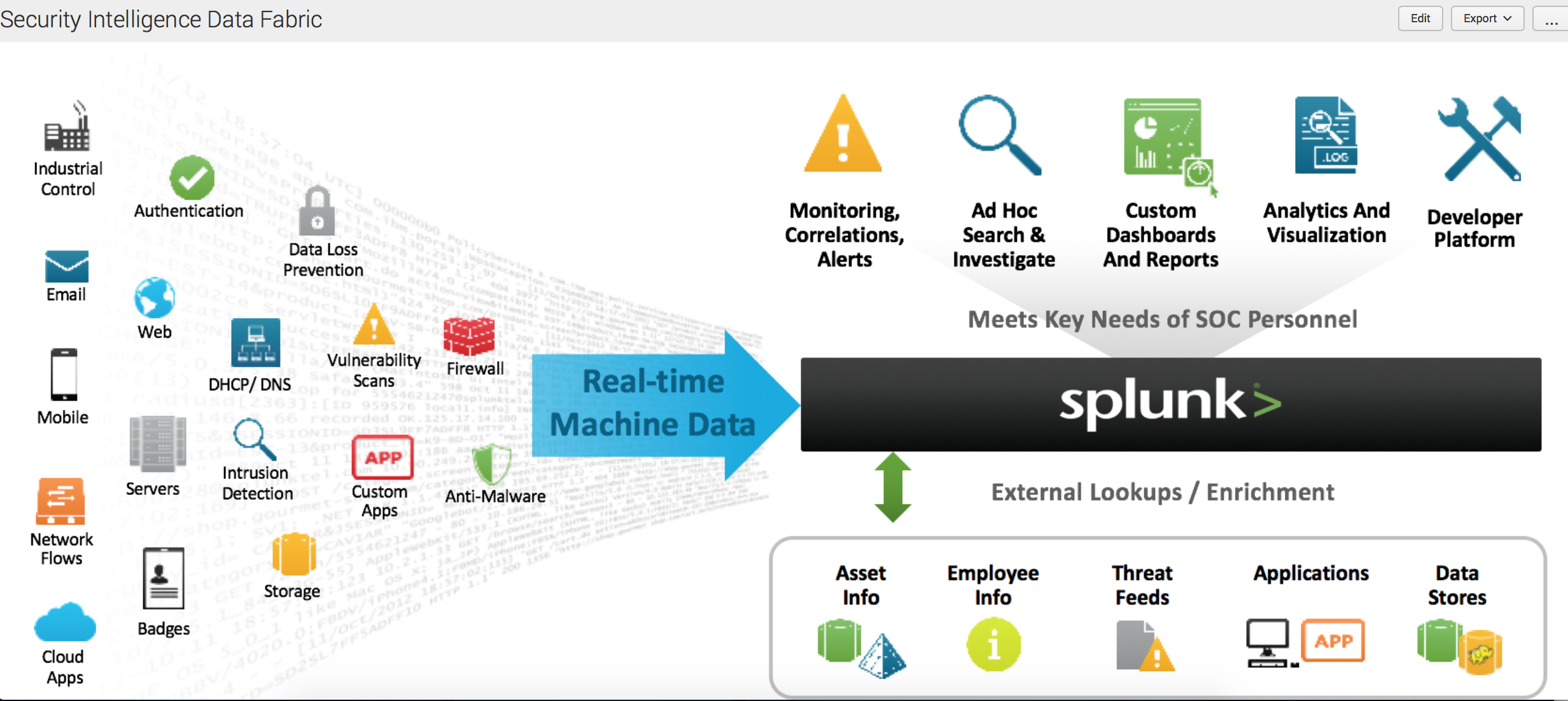
I thank for the information, now I will know.