Splunk lookup table
For information about the types of lookups you can define, see About lookups in the Knowledge Manager Manual. Note: The lookup command can accept multiple lookup and event fields and destfields. For example:. See Command types, splunk lookup table.
You can match fields in your events to fields in external sources, such as lookup tables, and use these matches to add more information inline to your events. You can also use the results of a search to populate the CSV file or KV store collection and then set that up as a lookup table. After you configure a fields lookup, you can invoke it from the Search app with the lookup command. You have a field lookup named dnslookup which references a Python script that performs a DNS and reverse DNS lookup and accepts either a host name or IP address as arguments. You can use the lookup command to match the host name values in your events to the host name values in the lookup table, and add the corresponding IP address values to your events. Was this documentation topic helpful?
Splunk lookup table
Splunk has some enormously powerful features for analyzing data. One of the most popular is the ability to take highly analytical information and render it in ways that are understandable by everyone. This feature is referred to as data enrichment. The function that enables data enrichment is built into Splunk processing language and is called lookups. What are Splunk Lookups? Lookups provide the ability to substitute cryptic information with more readable information without altering the meaning. If you had to create a report on the successful and unsuccessful Web page hits you would not want your audience to ponder; what is the meaning of ? Or what is the meaning of ? You can use a Lookup to take the cryptic value of and render the human readable equivalent of OK. You can use a lookup to provide additional information to a search from a separate file.
Also referred to as a static lookup because CSV files represent static tables of data. Prerequisites for knowledge management. Evaluate and Manipulate Fields.
Lookups enrich your event data by adding field-value combinations from lookup tables. Splunk software uses lookups to match field-value combinations in your event data with field-value combinations in external lookup tables. If Splunk software finds those field-value combinations in your lookup table, Splunk software will append the corresponding field-value combinations from the table to the events in your search. You can create lookups in Splunk Web through the Settings pages for lookups. If you have Splunk Enterprise or Splunk Light and have access to the configuration files for your Splunk deployment, you can configure lookups by editing configuration files.
The following are examples for using the SPL2 lookup command. To learn more about the lookup command, see How the SPL2 lookup command works. This example appends the data returned from your search results with the data in the users lookup dataset using the uid field. The third event is missing the department. The fourth event is missing the department and the uid. When you run the following search, for search results that contains a uid field, the value in that field are matched with the uid field in the users lookup dataset. The username and department fields from the users lookup dataset are appended to each search result.
Splunk lookup table
This lets you search for events when you do not know the specific error code. Was this documentation topic helpful? Please select Yes No.
Supplyworks net 30
Time Format Variables and Modifiers. Get started with table datasets Manage table datasets Define initial data for a new table dataset View and update a table dataset Dataset extension Accelerate table datasets. SURGe Access timely security research and guidance. Saving searches Scheduling searches. Fields and field extractions. Splunk Dev Create your own Splunk Apps. Lookup Command The lookup command provides match field-value combinations in event data with field-value combination inside an external lookup table file or KV-STORE database table. You can use this field lookup to add information from the lookup table file to your events. Search in the CLI. Splunk Answers Ask Splunk experts questions.
For information about the types of lookups you can define, see About lookups in the Knowledge Manager Manual. Note: The lookup command can accept multiple lookup and event fields and destfields. For example:.
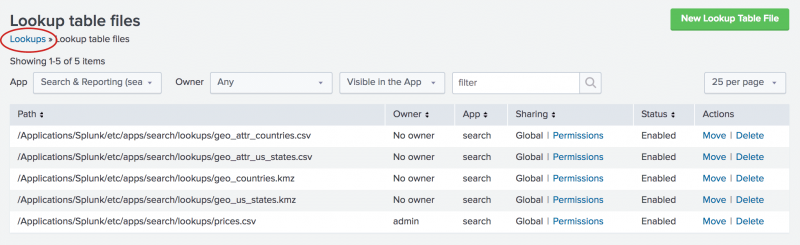
Configure a time-based lookup. A geospatial lookup matches location coordinates in your events to geographic feature collections in a KMZ or KML file and outputs fields to your events that provide corresponding geographic feature information encoded in the KMZ or KML, like country, state, or county names. Customer Stories See why organizations around the world trust Splunk. You can do this by creating a lookup definition in the Splunk web interface and configuring it to use an external file or database as the data source. Related Topics. Customer Success Customer success starts with data success. Manage knowledge objects through Settings pages Monitor and organize knowledge objects The sequence of search-time operations Give knowledge objects of the same type unique names Develop naming conventions for knowledge objects Understand and use the Common Information Model Add-on Manage knowledge object permissions Manage orphaned knowledge objects Disable or delete knowledge objects About Splunk regular expressions. All commands following the lookup are also processed on the local federated search head. Use automatic lookups to apply a lookup to all searches at search time. Please try to keep this discussion focused on the content covered in this documentation topic.

What remarkable question
I congratulate, it seems brilliant idea to me is